Tips On How To Create A Crypto Pockets: Best Practices For Builders
Active participation in crypto forums, Telegram groups, and Discord channels fosters belief and loyalty amongst users. Internet Hosting buying and selling competitions, giveaways, and airdrops can additional enhance user engagement. Furthermore, providing 24/7 buyer help is crucial for user retention. Merchants expect quick resolutions to issues related to deposits, withdrawals, commerce execution, and security considerations.
Selecting a safe crypto wallet is about extra than simply brand recognition—it’s about understanding the options that defend your funds from theft, loss, or unauthorized access. Whether Or Not you’re using a hardware pockets for long-term storage or a cellular pockets for daily transactions, some security features are non-negotiable, whereas others add valuable layers of protection and usability. Artificial intelligence will transform crypto wallets from merely passive storage devices to intelligent safety systems. Since phishing attacks and wallet-draining scams are becoming more and more refined, AI-based fraud identification would be the key function in such wallets. These wallets will track person habits, detect oddities, and block unauthorized transactions in actual time. The path to changing into a blockchain developer is a multifaceted journey that begins with a robust grasp of core blockchain ideas, corresponding to decentralization, immutability, and cryptographic safety.
The Method To Make A Crypto Pockets For Bitcoin And Different Cryptocurrencies
A paper pockets is a printed document that accommodates your personal and public keys. It’s an offline storage method, making it one other wallet possibility for long-term storage. Paper wallets are ideal for customers who want a simple and cost-effective solution.
Vulnerabilities in the wallet—via personal key misuse, phishing or good contract exploits—remain high of thoughts. An efficient learning technique typically entails a synergistic blend of these sources. Steady studying, fueled by engagement with blogs and active developer communities, then ensures that this knowledge stays present.

Some of the good examples of public libraries are Chain-Java and BitcoinJ. For them, it’s a extra handy approach to obtain wages compared to a daily financial institution transfer. One method to settle for a Bitcoin salary without any downside is to create a wallet tackle so that the employer will pay the month-to-month Bitcoin quantity. It means that even understanding the wallet address, it’s impossible to find out the recipient. You can implement established smart contract libraries like OpenZeppelin for ERC-20 to stop errors with sensible contracts. Additionally, you presumably can consider making use of a checks-effects-interactions sample to avoid reentrancy cyber assaults.

One of the most thrilling developments is reward-based security measures. People who allow multi-factor authentication (MFA) or maintain funds in non-custodial wallets for prolonged durations can receive loyalty points or staking rewards. Most DApps include a frontend (the person interface) that communicates with smart contracts (which act because the backend logic residing on the blockchain). This typically means that DApp builders need to possess a full-stack skillset tailored to the Web3 environment. These computer science fundamentals aren’t merely theoretical prerequisites; they form the unseen scaffolding that helps the event of robust, environment friendly, and safe blockchain applications.
- Extra costs like advertising, buyer help, and liquidity partnerships additionally play a job.
- With the assistance of these keys, you’ll be able to ship or obtain cryptocurrency whereas preserving your personal key completely encrypted.
- This information delves into the pivotal features of crypto wallet development as we venture into 2025.
- Importing paper wallets permits crypto holders to switch funds between a bodily paper wallet and the digital crypto wallet app.
- Solana may be thought-about a blockchain choice for wallet development, contemplating the fast transactions and low fees.
- Trezor and Ledger Nano are hardware wallets that keep a user’s personal keys on a hardware gadget, isolated from internet threats.
Offering bonuses, trading charge discounts, or profit-sharing mechanisms to associates and influencers can drive engagement. Buying And Selling simulations and order-matching tests are additionally essential to verify the effectivity of trade execution, liquidity management, and market operations. In The Meantime, paper buying and selling simulations assist assess commerce execution velocity, ensuring the graceful processing of buy and promote orders. Not to neglect, a user-friendly interface is important for attracting merchants. A strong authentication system is essential for shielding person accounts.
Design Tools
A hardware pockets is a physical gadget that securely shops your P-keys offline. It’s one of many safest options for storing giant quantities of cryptocurrency or holding property long-term. These wallets act as cold wallets, keeping your funds protected from online threats. They are dearer however supply unmatched security for users who value safety above all. Lastly, choose the wallet utility type corresponding to custodial/non-custodial, cold/hot, multisig, and its subsequent options like personal key storage, multi-currency support, security parts, and so forth. Key management is a should have feature of cryptocurrency pockets software as it elucidates the methods those keys are saved.
This approach reduces complexity and may help you identify a firm footing in the trade. Layer 2 options like zk-rollups and optimistic rollups may even play a big function, lowering fees while maintaining security. Post-quantum cryptography and confidential computing will play an increasing position. Safe enclaves enable protected information processing even on compromised machines. Refined adversaries use targeted assaults, AI-enhanced phishing, and blockchain-specific exploits to realize unauthorized entry. We advise and accompany medium-sized companies on their ongoing path to digital transformation.
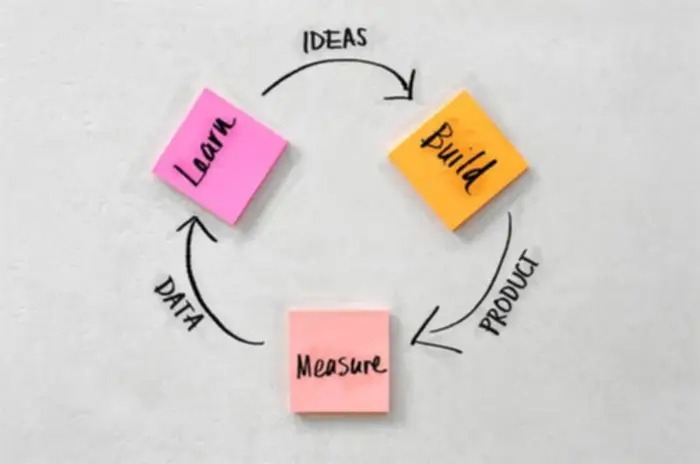
Wallets have gotten gateways to the decentralized internet, letting users work together with dApps, marketplaces, and DAOs with out leaving the app. Wallets with built-in Most Extractable Worth (MEV) safety prevent users from being exploited in DeFi trades, guaranteeing Data Mesh honest transactions. Creating an MVP isn’t simply sensible – it’s essential for mitigating risks and guaranteeing your pockets resonates with its intended audience. From performance to safety, each side of your wallet have to be scrutinized.
While it might sound counterintuitive in the digital age, paper crypto wallets still maintain a singular place on the planet of cryptocurrency storage. Primarily, a paper pockets includes printing out your public and private keys on a piece of paper, which you then store securely offline. This technique provides an added layer of security by keeping the keys fully off the internet, thus making them proof against hacking makes an attempt.
You can use a pockets app in your cellphone or computer to handle your funds easily. When you create a crypto wallet, you have to choose one that matches your wants and is safe. There are several varieties of crypto wallets, like software wallets, hardware wallets, and paper wallets. Cryptocurrency pockets growth entails making a software program program that keeps non-public and public keys, permits customers to ship and get digital foreign money, and tracks their stability. However, unlike how to build a crypto wallet the tangible pockets in your pocket, a cryptocurrency wallet does not retailer money. Instead, it data transactions on the blockchain, reflecting changes in balances.
If you retailer your private keys or seed phrases incorrectly or insecurely, like in digital files or cloud storage, they are often stolen by decided attackers. Transaction errors, like you might see when sending funds to the wrong tackle and even the wrong community, can lead to irreversible loss. Although hardware wallets introduce an additional step in comparability with software options, they excel at safeguarding giant balances and long‑term holdings.
Determine the necessary thing areas where your product can stand out among the many opponents with distinctive features or enhancements. Use the outcomes of your research to make data-driven decisions and construct a robust digital pockets for cryptocurrency. This function permits customers to perform the funds instantly from their crypto wallets, via the integrated exterior payment processors or gateways for cryptocurrencies.
A QR Code Scanner characteristic adds velocity, comfort, simplicity, and safety to your crypto wallet app transactions. Here are the important options that you have to embody in your crypto wallet app. Additionally, crypto wallets have numerous applications for enterprise use. Companies can develop their own https://www.globalcloudteam.com/ crypto wallets and combine them with cost techniques and other enterprise solutions.